ENIGMA Chapter 3 – The Substitution Cipher
ENIGMA Chapter 1 – Historical Background
ENIGMA Chapter 2 – The Invention of the Enigma Machine
The Enigma machine is a polyalphabetic substitution cipher machine. This post will provide a little background information on the differences between monoalphabetic and polyalphabetic substitution ciphers and on the specific characteristics of cipher alphabets created by an Enigma machine.
Monoalphabetic and polyalphabetic substitution ciphers
In a substitution cipher system a single unit of plaintext (a letter, a group of letters, a number, etc) is replaced by a different unit according to a regular system. When a monoalphabetic substitution cipher system is used, an entire text is encoded with a single fixed cipher alphabet, like the one shown in Figure 1. In this example, A is always replaced by B, B by V, and so on. If you use it to encode the plaintext THE IMITATION GAME, the resulting ciphertext is HAK DSDHBHDOE NBSK.
A monoalphabetic substitution cipher can easily be broken using frequency analysis. In every language, certain letters are more common than others, e.g. in English E is the most frequent letter, whereas others like X and Z are rarely used. Therefore, if the letter K is the most common letter in a ciphertext, it is very likely that it stands for the letter E. General knowledge of a language’s structure, common words and phrases is also useful when deciphering an encoded text.
The cipher alphabet shown in Figure 1 is not reciprocal. This means that while A is replaced by B, B is not automatically replaced by A but by a different letter (V). It is also possible for a letter to encode itself, as in O does in this case. We will soon see how this differs from a cipher alphabet created by an Enigma machine.
Polyalphabetic substituion ciphers are more complex, as the cipher alphabet changes during encryption.
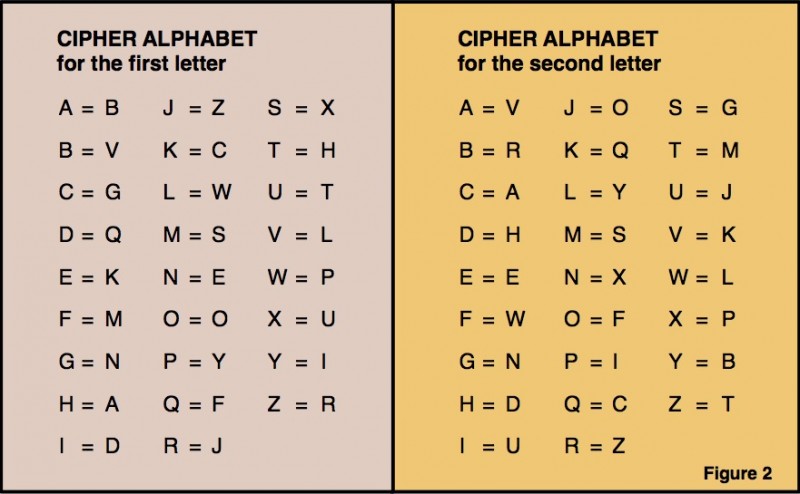
Figure 2 shows two different cipher alphabets, one for encoding the first letter of plaintext and the other for the second letter. The word TO is encrypted by looking up T in the first cipher alphabet (T-> H) and O in the second (O->F), resulting in the ciphertext HF.
Enigma – a polyalphabetic substitution cipher machine
The Enigma machine created a different cipher alphabet for every consecutive letter of plaintext. Two important characteristics were the result of the so-called reflector, which we will look at in more detail later: (1) the alphabet was reciprocal and (2) a letter could never be encoded as itself.
- Cipher alphabets created by an Enigma machine were reciprocal. This means, for example, that if the letter A was encoded by U, then U was encoded by A. If you pressed A on the keyboard, the letter U lit up on the lampboard; if you pressed the key for U, A was illuminated. Consequently, encoding and decoding were mirror processes. If you set up two Enigma machines exactly the same way, typing a plaintext on one delivered an encoded ciphertext, and if you typed this ciphertext into the other machine using an identical setting, the result was the original plaintext.
For example: An operator set up an Enigma machine to encipher the plaintext THEXIMITATIONXGAME (the letter X indicated a space). Pressing the key for the first letter T illuminated the letter F on the lampboard. The operator wrote down F and then typed the next plaintext letter H, which lit up I, and so forth. The final result was the ciphertext FILRQ HLHXH ULMMZ MZT (letters were written down in groups of five). The ciphertext was then transmitted by a radio operator using Morse code.
The receiver picked up the radio signal and translated the Morse code back into the ciphertext. If the operator on the receiving end knew the sender’s setting and set up the Enigma machine the same way, typing the ciphertext FILRQ HLHXH ULMMZ MZT produced the plaintext THEXIMITATIONXGAME.
The Enigma machine could thus be used for both encoding and decoding.
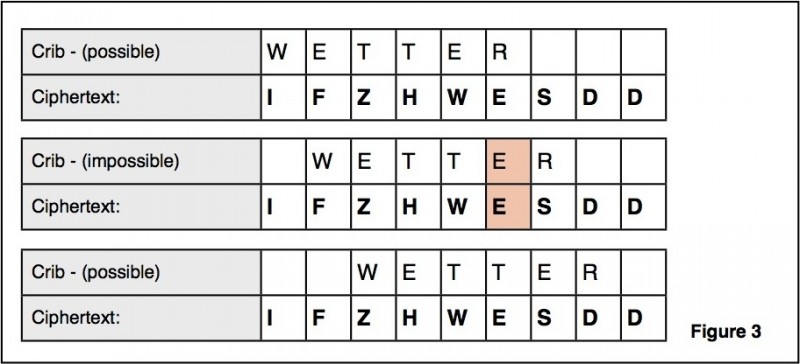
- A letter could never be encoded as itself. This feature proved to be extremely helpful to codebreakers during World War II. Cryptanalysts looked at a ciphertext trying to guess the position of words or phrases they expected to find (like WETTER i.e. weather). Codebreakers at Bletchley Park called these fragments cribs. An easy way to determine whether a crib was a possible solution, was to place it over the ciphertext and check to see if any letters were identical. If so, they knew that this guess was incorrect. Figure 3 shows three such guesses; the first and the third are possible, the second one is not because E can never be replaced by E.
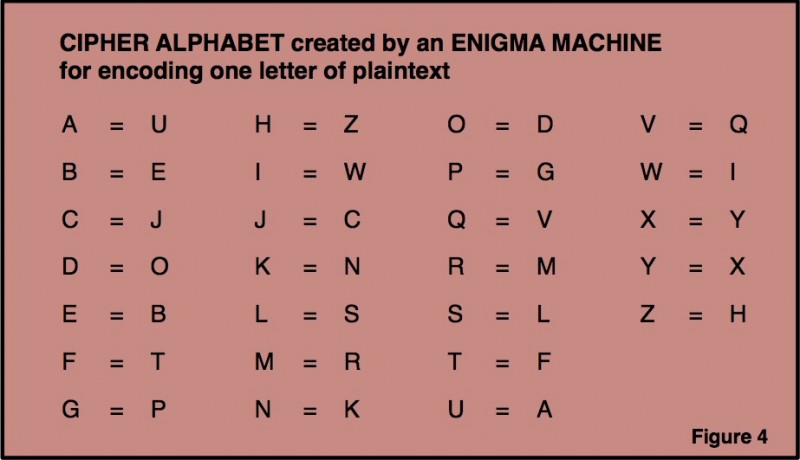
Both characteristic features can bee seen in this cipher alphabet, created by an Enigma machine for encoding one letter of plaintext (Figure 4). A is encoded by U, and thus U is automatically encoded by A. B is replaced by E, so E is replaced by B, and so on. No letter is encoded as itself.
Part 4 will take a closer look at how the Enigma machine worked and how it created this large number of different cipher alphabets.
—
Previous posts:
ENIGMA Chapter 1 – Historical Background
ENIGMA Chapter 2 – The Invention of the Enigma Machine
Next post: ENIGMA Chapter 4 – How Does the Engima Machine Work? (Part 1 – The Elements of an Enigma Machine)
FURTHER READING:
Books:
SINGH, Simon. The Code Book – The Secret History of Codes and Code-Breaking. London, 1999
Articles:
SAUERBERG, Jim. Cryptology: An Historical Introduction DRAFT. 2006 http://galileo.stmarys-ca.edu/jsauerbe/bookshort.pdf and http://galileo.stmarys-ca.edu/jsauerbe/m10s11/ (Retrieved April 2014)
Websites:
SALE, Tony. Substitution cipher and the principle of the Enigma http://www.codesandciphers.org.uk/enigma/enigma1.htm (Retrieved April 2014)
Crypto Museum: Enigma: http://www.cryptomuseum.com/crypto/enigma/index.htm (Retrieved April 2014)
—
Enigma Image: http://upload.wikimedia.org/wikipedia/commons/7/74/Bundesarchiv_Bild_101I-241-2173-09,_Russland,_Verschlüsselungsgerät_Enigma.jpg




Write a comment
You need to be logged in to leave a comment.